Vitalpointz IoT Core/Core Lite offers variety of device security mechanisms. They are –
SSL VPN vitalpointz IoT Core/Core Lite bundles OpenVPN (an open source VPN server) service with it. Every Fog Node establishes VPN Tunnel and transacts with the Cloud platform over VPN.
Secure connectivity vitalpointz IoT Core/Core Lite provides secure connectivity services by default. Every device that is Registered/ Added under vitalpointz IOT Core/Core Lite is generated with a private Key and Certificate. These are used to connect to MQTT service over TLS. For the devices incapable of connecting using MQTT over TLS, HTTPS REST based message publishing APIs are provided to send messages to Cloud Platform securely.
Mutual Authentication Device certificate is used by server to verify the authenticity of the device, while device verifies Server authenticity using Root Certificate.
Topic Whitelisting Each Device is allocated with a top-level topic name space by vitalpointz IoT Core/Core Lite Platform. The topic looks like v/yaP4HaCFg. A leading character and a unique alphanumeric short string separated by a /. Device programmers are free to create any number of sub topics under the name space, however they are not allowed to use totally new parent topic.
For example, a topic of v/yaP4HaCFg/sensor1/field1 is allowed.
The top level device topic is whitelisted and any other topic is not allowed to pass the Platform. The Device topic allocated to the device can be viewed by clicking on the device card on the Web Ui. The Slider component shows the topic.
Blocking/Unblocking Device User can block the device by clicking on the menu item of the card representing the device. This has the effect of black listing the device topic. Unblocking removes the black listing and allows the device topic to be forwarded again. This is useful when the device is connecting using insecure connectivity service, revoking certificate will not have any effect in that situation.
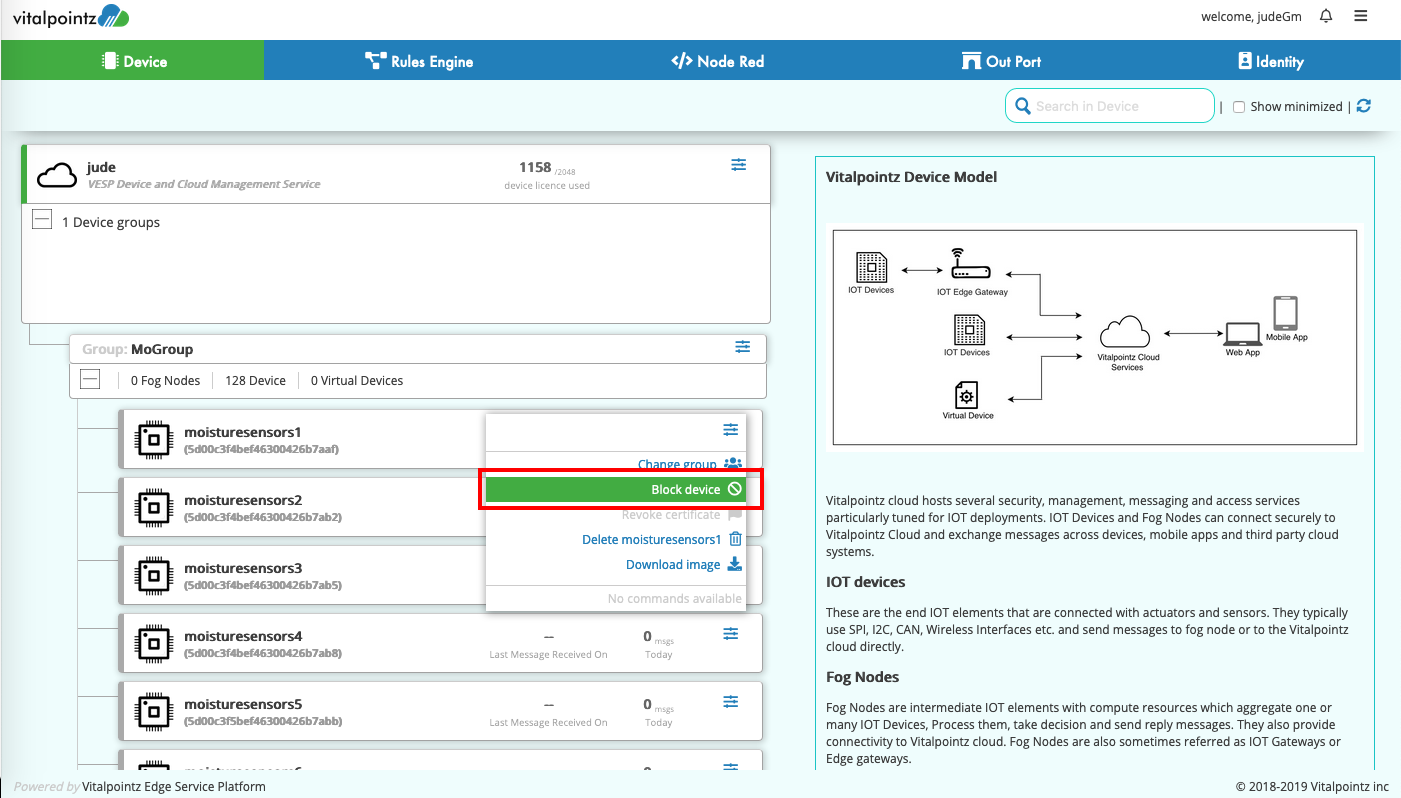
Note: Blocked Device will be able to make TCP connection to MQTT Service. Only the message is dropped after inspecting the topic.
Revoking/Re-Issuing Certificates Sometimes user might want to suspend the device by disallowing it even to make TCP Connection. In such scenarios, Certificate Revocation feature will be helpful. By invoking this option, the device certificate is added into CRL file of the MQTT server. Resulting in TCP Connection failing when the Device attempts to make a connection. Reissuing the certificate will reverse the process and issue new certificate. When the Device reboots vESPA runs as part of device startup process, vESPA downloads new certificates. Thus, the Device continues normal operation.
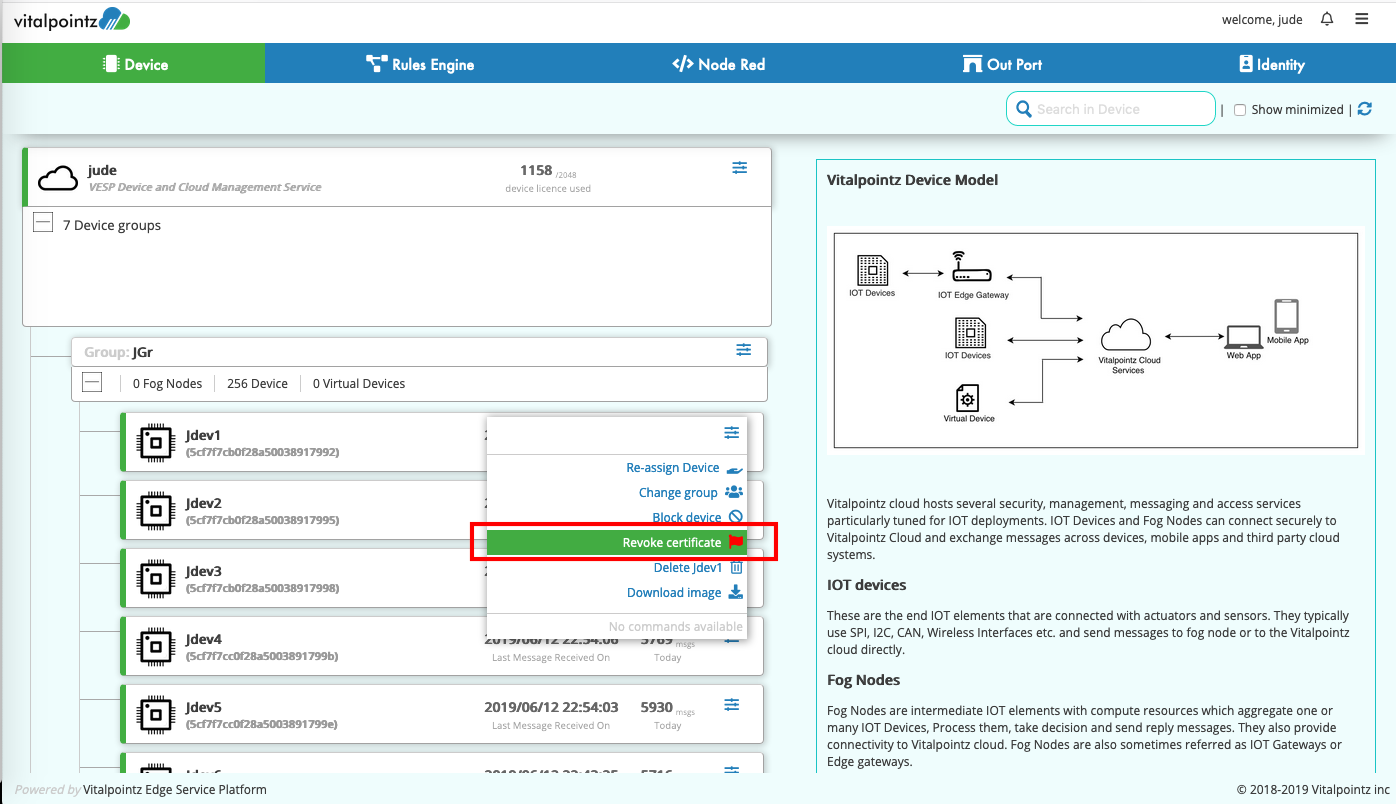
Note: Revocation of certificate just creates certificate revoke list. In order to apply the changes, MQTT-TLS service needs to be restarted by clicking ‘Restart MQTT Server’